Blog, Breaches, Trusted Security Advisor, Digitalera, Partner News, Ransomware Detection, All, cybersecurity, ITsupport, securityawareness, MFA, multifactor, passwords, ransomwareprotection, ransomware, DDoS
5 Steps to Skyrocket your Cybersecurity
5 Steps to Skyrocket your Cybersecurity
Author:
Ricardo Martinez
Chief Revenue Officer
DigitalEra Group.
Why the need to Skyrocket your Cybersecurity?
There's a lot of things going on in the cybersecurity landscape. Cyber is top of mind everywhere. If you listen to the news at any time during any day, you're going to hear something about a cybersecurity incident. This year has been very active with hacks like the Colonial Pipeline, JBS, Kaseya... So it's an ongoing threat affecting companies in every single industry, which will continue happening.
The bottom line is today we have a huge dependency on digital. In the past, probably incident and hacking wasn't really going to affect our business, but now a hundred percent of it affects our business; digital communications, information, everything nowadays is digitized. So our dependency has made us even more susceptible to cyberattacks, threats, and ransoms. The dramatic increase in threats is due to our way of doing business nowadays. Transactions, digitalization, everything is now online. Money moving digitally is a big one, and the threat actors know that. So they will try to get us where it hurts and they'll try to get what can make a profit for them.
Common Attack Vectors
The primary threat has been ransomware. We've seen a lot of organizations get hit by ransomware because it's just an easy way of monetizing a hack and monetizing malware. Hackers extort your company, you're very susceptible to that because you need your business to have continuity, and you will likely pay to release those encrypted files.
The following are also common threat attack vectors:
- Denial of Service and Distributed Denial of Service.
- Compromised credentials
- Phishing
- Weak Passwords
- Software Vulnerabilities
So what are the 5 Steps to Skyrocket your Cybersecurity?
1. Know your numbers:When we talk about numbers we may pose the following questions:
What are the numbers of alerts that I'm getting? How many viruses have I blocked today? Number of incidents? Number of attacks? Number of mitigated incidents? Number of vulnerabilities?

Though it's good to know these numbers, this won't necessarily give you a sense of your cybersecurity posture. It would most likely show you the value your security tools are providing.
So when we say Know your Numbers, we're referring to understanding the controls you have in place. How do you measure that? Are you following a specific cybersecurity framework? Are you implementing the right security tools? What percent of completion do I have of those security controls? Am I implementing the security programs? These are the numbers you want to actually understand in order to get a sense of your cybersecurity posture.
2. Assess your Readiness
How prepared are you in the event of a breach? If you've been breached, now what? How do you take action? You need to understand if you have things in place that can help you mitigate.

Instead of having the breach happen and then trying to figure out what to do, try to plan ahead instead. A good start would be by developing an Incident Response Plan. There are actually free templates out there you can leverage for this. You can put into place playbooks that will guide you in the event of a breach, so you're not caught off guard.
Another thing that you'd want to consider is having cyber insurance. Do you already have a policy in place? Is it the right policy? Is it going to cover your needs?
Also when assessing your readiness or preparedness, you should look into next-gen anti-malware products to minimize the impact of ransomware. Another one is a multi-factor authorization (MFA), given a lot of breaches occur due to weak passwords or credentials. And finally, having a vulnerability management program is also a must.
3. Pick the Quick Wins
Identify what can have the greatest impact with the least cost:
-
- Incident Response Plan?
- Next-Gen AV?
- Process Review?
- Mandatory MFA?
4. Fill in the Gaps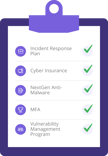
Start implementing those quick wins, there are multiple things you can implement after you do the readiness assessment in order to fill in those gaps that will dramatically improve your security posture. Take the time to develop these plans and programs and execute them accordingly.
5. Get Expert Help
There's a lot of great information out there which is fairly easily accessible. Becoming a part of an association, building a network through LinkedIn, joining groups, and seeking to connect with knowledgable people and peers within the industry for advice on making decisions to really improve your security posture.
Also, rely on consultants such as DigitalEra Group, and have them assess where you are and what you need to improve your security posture. If you don't have a CSO, consider getting a virtual CISO; bring someone from outside that has the expertise to build out your program, identify your gaps and help you fill them.
A great option is always to turn to the security vendors you're already working with; they often have a lot of free advice.
And finally, makes sure that you have a trusted advisor. You'll have a lot of peace of mind knowing you can rely on an organization that will give you the best information and not necessarily tries to sell you on a specific technology.
If you're interested in more details about each of these steps to Skyrocket your Cybersecurity, watch the recorded presentation below where I talked about this at our recent Secure Miami virtual event.
Ricardo Martinez, Chief Revenue Officer, DigitalEra Group.
About DigitalEra
DigitalEra is a leading solution provider of network and cybersecurity products and services, serving major business, education and governmental agencies throughout the US. In addition to access to the most sophisticated and effective security products, DigitalEra provides expert guidance on use as well as ongoing security counsel and insights that help their clients prevent security breaches and mitigate threats. For more information, visit:www.digitaleragroup.com.
